Checkpoint have made a tool to forward checkpoint logs to SIEM systems.
It is possible to filter specific logentries out from being forwarded to the siem system using this tool, but it depends on what format you are using.
I currently work with LogRhythm SIEM systems, and here it is possible (with great granularity) to specify which log entries is being sent.
For more info see Checkpoint sk122323
First we will configure the log exporter to forward logs to our SIEM system.
Log in to your Checkpoint Manager or Log Server in Expert mode.
[Expert@GW1:0]# cp_log_export add name TEST target-server 192.168.1.3 target-port 514 protocol tcp format logrhythm read-mode semi-unified
Export settings for TEST has been added successfully
To apply the changes run: cp_log_export restart name TEST
[Expert@GW1:0]#
[Expert@GW1:0]#cp_log_export restart name TEST
Stopping log_exporter for: TEST
Starting log_exporter for: TEST
cpwd_admin:
Process EXPORTER.TEST started successfully (pid=29053)
Just to be sure – run this command. Sometimes the exporter starts successfully, but do not show that it stops again.
[Expert@GW1:0]# cp_log_export status
name: TEST
status: Running (29053)
last log read at: 7 Apr 20:46:52
debug file: /opt/CPrt-R81/log_exporter/targets/TEST/log/log_indexer.elg
Now the log exporter is running and you should see logs streaming in on your SIEM system.
So lets proceed to the second part, filtering in the logentries we want to forward to our SIEM system.
We need to edit two files in order to do this…
[Expert@GW1:0]#cd $EXPORTERDIR/targets/TEST/
[Expert@GW1:0]# ls
conf data fieldsMapping.xml log log_exporter log_indexer_custom_settings.conf targetConfiguration.xml tmp
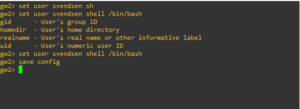
[Expert@GW1:0]#vi targetConfiguration.xml (We will in this file point to a configuration file in the conf directory)
Change the configuration to this…
From:<mappingConfiguration></mappingConfiguration>
To:<mappingConfiguration>conf/LogRhythmFieldMapping.xml</mappingConfiguration>
From: <exportAllFields>true</exportAllFields>
To:<exportAllFields>false</exportAllFields>
Save and exit. (If you have trouble saving lookup vi or vim editor for basics)
Now we will edit the second file “LogRhythmFieldsMapping.xml” in the conf directory
[Expert@GW1:0]#cd conf
[Expert@GW1:0]# ls
Bookmarks.xml FilterConfiguration.xml JsonFieldsMapping.xml LeefFieldsMapping.xml LogFields.xml SplunkFieldsMapping.xml _local_ckp.linux50.tmp filter_tree.xml log_indexer_settings.conf tmp_FastEvent_log_fields.C
CefFieldsMapping.xml GenericFieldsMapping.xml JsonFormatDefinition.xml LeefFormatDefinition.xml LogRhythmFieldsMapping.xml SplunkFormatDefinition.xml fields-enums.xml ip2country.csv smartlog_unification_scheme.C
CefFormatDefinition.xml GenericFormatDefinition.xml LaaSFieldsMapping.xml LogFamilyFields.xml LogRhythmFormatDefinition.xml SyslogFormatDefinition.xml fieldsMapping.xml log_fields.C targetConfigurationSample.xml
[Expert@GW1:0]#
[Expert@GW1:0]#vi LogRhythmFieldsMapping.xml
Edit the LogRhythmFieldMapping.xml to the support your needs.
The default setting is “true” which means that the field is sent in the log file.
Changing this to “false” will exclude the log entry from being forwarded to the remote syslogserver.
Example – exclude the “user” field in the logentry from being forwarded to the remote syslogserver.
The original entry looks like this.:
<field>
<exported>true</exported>
<origName>user</origName>
<dstName>User</dstName>
</field>
Change the “true” to “false” so the entry looks like this.
<field>
<exported>false</exported>
<origName>user</origName>
<dstName>User</dstName>
</field>
After we are done editing our “target” configurations, we need to restart the log exporter tool.
[Expert@GW1:0]# cp_log_export restart
Stopping log_exporter for: TEST
cpwd_admin:
Process EXPORTER.TEST (pid=29053) stopped with command “kill 29053”. Exit code 0.
Starting log_exporter for: TEST
cpwd_admin:
Process EXPORTER.TEST started successfully (pid=894)
[Expert@GW1:0]# cp_log_export status
name: TEST
status: Running (894)
last log read at: 7 Apr 21:09:24
debug file: /opt/CPrt-R81/log_exporter/targets/TEST/log/log_indexer.elg
[Expert@GW1:0]#
Now the “user” field is not being forwarded to your SIEM system.
(But it is – i can see two more entries with the user field !)
Well… thats because there is three fields in the LogRhythmFieldMapping.xml file containing a “user” field… edit them all out, then everything will work as expected 🙂
So to summon things up…
1. configure the cp_log_exporter
2. Edit the targetConfiguration.xml file
3. Edit the LogRhythmFieldMapping.xml file
4. Restart the exporter tool.
A big Thanks goes to Alon from Checkpoint, for explaining to me how this feature worked !