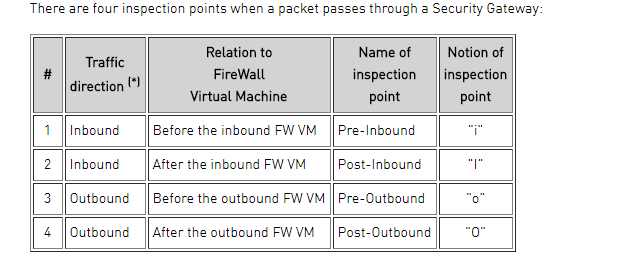
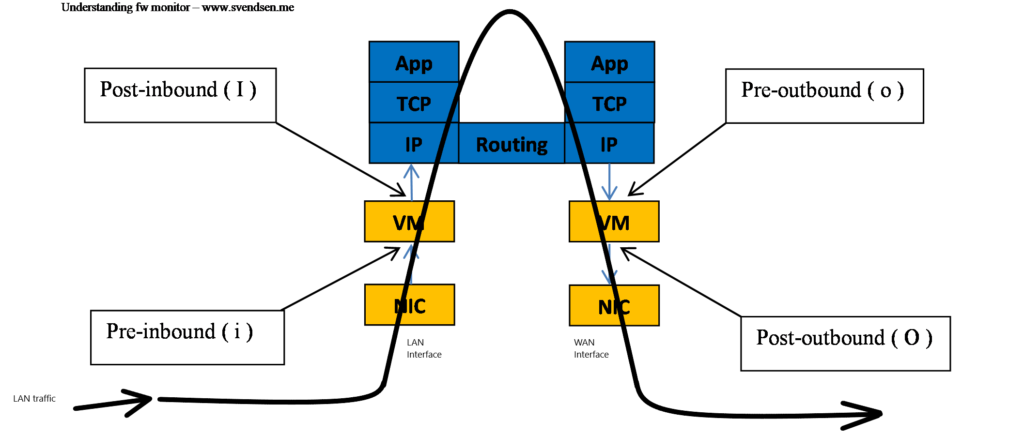
The other day i was performing troubleshooting on a firewall, and wanted to make a capture using fw monitor.
As i normally do, i performed the commands mentioned in sk30583 with the ”-e” flag, but the other day i got an error.
Then i remembered… going forward from R80.x they made some new commands.
I don´t really know when or why this only impacts some of the R80 systems, (and i have not spend time researching this topic) but my guess is that it is dependant on the patchlevel of the system.
Anyway – the new commands can also be found at checkpoint Sk30583.
Go to chapter 8 ”Capture Examples of “-F” flag”
Example.
(Remove the brackets from the command)
fw monitor -F ”{src IP}, {src port}, {dst IP}, {dst port}, {protocol number}”:
Example captureing ssl trafic on port 443.
fw monitor -F ”0, 0, 0, 443, 0”
Example capturing traffic from source ip
fw monitor -F ”10.10.10.10, 0, 0, 0, 0”